NOTE: post updated Jan 3 2008
In all likelihood, you, or someone close to you, has a computer that is infected with a Trojan horse program. Current estimates are that at least 50% of home computers running Microsoft Windows are infected. These programs, such as the Gozi Trojan I described here, are being used to steal identity information, such as bank account numbers and passwords. And, the bad guys are getting very good at using that information to create forged bank cards and to conduct fraudulent transactions with your money.
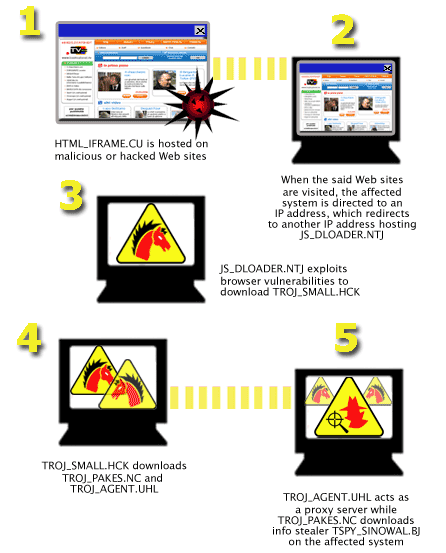
 Even careful Internet users are at risk. When a new computer is connected to the Internet, it will be attacked by active scanners within 5 minutes and any vulnerabilities will be exploited. Newer Trojans can also infect users when they simply visit compromised web sites, without the knowledge of the web site owner or the end user. Anti-virus software is not completely effective in detecting these bad programs, and new Trojans are launched every day.
Even careful Internet users are at risk. When a new computer is connected to the Internet, it will be attacked by active scanners within 5 minutes and any vulnerabilities will be exploited. Newer Trojans can also infect users when they simply visit compromised web sites, without the knowledge of the web site owner or the end user. Anti-virus software is not completely effective in detecting these bad programs, and new Trojans are launched every day.
So, how can we continue to do financial transactions, such as Internet banking, in the face of these threats? The problem is that the personal computer is a general purpose machine that is good for banking, but it also can be used for lots of other things at the same time, such as running Trojan programs. What we need is a computer that will only do Internet banking when we are doing financial transactions.
One practical solution is to reconfigure your computer for financial transactions so that there is less likelihood that it will be running bad programs during your banking session. This is where “boot CDs” (also called Live CDs) come in. By starting the computer with a boot CD, we can configure it in a way that is safer for financial transactions. We can start a fresh operating system and a clean Internet browser and, since CDs are read-only devices, the CD can never get infected and will always be clean. At least one bank is starting to distribute Live CDs to their customers.
I am currently looking for Live CDs that are suitable for Internet banking. I don’t know of any Live CDs that provide a Windows environment, and Windows computers can be infected very quickly, so I am looking at Linux. Most of the major Linux distributions will boot and run from the CD. These Live CDs tend to start a complete, full-featured Linux environment in order to show off all the features of the distribution, and to support a full install on the hard drive. This slows down the boot time and makes for a complicated, unfamiliar user interface. What we need is a minimalistic Live CD that only starts the programs we need to do our Internet banking.
Over the past few weeks I have acquired a collection of Live CDs, and quickly developed a list of requirements:
- easy enough to use so that I can give them away and not receive phone calls when things go wrong
- quick boot up
- automatic configuration of the network
- automatic launch of the browser, or at least obvious to find
- a familiar browser, such as Firefox 2
- should have browser extensions installed, at least Flash and PDF
When trying Live CDs with these characteristics, I have also uncovered a number of problems areas:
- doesn’t work on all machines. I use both brand new Dell computers and old, generic ones. Some of the Live CDs don’t work on all the computers I try them on, most notable the Dells
- low screen resolutions, sometimes as low as 640 X 480, with now way to make changes. Resolution should be at least 1024 X 768 and, ideally, be easily adjusted by the user at boot time, or once the system is started
- monitor refresh rates greater than 60 Hz. Many distributions only support a 60 Hz refresh rate, which works on LCD screens but looks terrible on older CRT monitors.
- bad browser fonts. The default fonts used within Firefox often look terrible in Linux distributions until the user configures the computer and browser. The Live CD should come with a good set of fonts.
- support for wireless networks. Most Live CDs can automatically detect and configured a wired network, but I have yet to find one that will work with a wireless network. This is crucial for people using laptops.
Here are the Live CDs I have found so far, with some comments. I group them into small, special purpose offerings, and large Linux distributions. I am updating the list and the comments as I learn more.
Small Environments
- Webconverger 2.14 (http://webconverger.com/) is my current favorite. It boots quickly and restricts the user to a Firefox browser. It seems to do a good job at setting the monitor to the maximum resolution and refresh rate. In fact, on one test machine I would have preferred 1024 x 768 on the cheap monitor instead of the 1280 x 1024 that was chosen, but the display was good. (On another new Dell machine, however, the resolution was set to 640 x 480 instead of the 1280 x 1024 that the LCD can display.) Flash, PDFs, and sound seem to work. My only complaints are that some of the familiar shortcut keys don’t work in the browser: CTRL-+ and CTRL– for controlling the font size, CTRL-T and CTRL-W for creating and closing tabs, and CTRL-K to get to the search form, and CTRL-L for moving to the address bar.
UPDATE: Webconverger 2.36 tried on Jan 3 2008: I just tried out this boot CD on a number of machines and it worked great. It did a good job of selecting a video resolution and frame rate on different types of monitors. I did run into a problem booting an HP Compaq desktop machine, but a quick Google search showed that this model has problems with all Linux distributions until you add acpi=off to the boot parameters. This is now easy to do in Webconverger.
- cl33n (http://cl33n.com/) boots quickly and launches Firefox automatically. In fact, it will only run Firefox. This environment works well, but it will not refresh the screen faster than 60 Hz and so does not handle CRT monitors. Also, sound does not work for me and Flash is not installed, but it can be.
- Damn Small Linux (http://www.damnsmalllinux.org/) did not work on my newest Dell machines and suffers from the 60 Hz problem
- KioskCD (http://www.kioskcd.com/) have not tried it yet
- Hospitality Machine Kiosk 1.0 (http://www.hospitalitymachine.co.uk/HospitalityMachineKiosk.htm) had problems on both machines I tested it on. On one machine it could not do a DHCP configuration on the network, similar to the SLAX offering. Most other environments do work on this machine. On the second machine the software would not boot, complaining that it could not find the Knoppix file system. (Note: I ran into the same problems with version 1.1.)
- SLAX 5.1.81.1 (http://www.slax.org) boots into text mode and requires the user to login as root. The user then runs xconf and startx to bringup the graphical environment, which does result in a good resolution and refresh rate. The browser is Konqueror, which is rather unfamiliar. On one of my test systems, the network was not configured using DHCP.
Complete Distributions
- Dreamlinux 2.2 RC3 (http://www.dreamlinux.com.br/english/index.html) is good at handling screen resolutions and refresh rates. During the boot process, the user is asked to choose the resolution and the refresh rate is automatically set correctly for LCD and CRT monitors. This is a complete Linux environment so the interface is a bit complex, but the Firefox browser is easy to find, the fonts are OK, Flash is installed, and sound works. It appears that a PDF viewer is not configured in Firefox by default, however. If you can handle choosing the resolution at boot time and a full Linux interface, I recommend this one.
- Knoppix (http://www.knoppix.org/) is a full Linux environment with a large collection of system and network tools designed for advanced users. I was able to set screen resolutions that I like and the system works well.
- Adiosweb 7.3 (http://os.cqu.edu.au/adios/adiosweb.html) is very close to a full Linux environment. The user has to make two rounds of decisions at boot time, and then login using a obscure password. The screen resolution was OK at startup and is configurable through the GUI interface. The fonts used within the web browser were not ideal, but this might be a good choice.
If you have any comments on these solutions or you know of other boot CDs to try, please let me know.



 When you buy sex toys, do you worry about your privacy? Would you pay more at Internet stores that displayed clear privacy information that addressed your concerns?
When you buy sex toys, do you worry about your privacy? Would you pay more at Internet stores that displayed clear privacy information that addressed your concerns? The results of the latest round of biometric testing are out, and face recognition systems have improved a lot. This is important because face recognition can be used for a variety of applications, including matching against ID photos on driver’s licenses and passports. Automatic face recognition can also be done covertly, at a distance, which has important privacy concerns.
The results of the latest round of biometric testing are out, and face recognition systems have improved a lot. This is important because face recognition can be used for a variety of applications, including matching against ID photos on driver’s licenses and passports. Automatic face recognition can also be done covertly, at a distance, which has important privacy concerns. Here is an interesting review of new authentication methods, including cognitive passwords, Pass Faces, and various biometric techniques. Although these techniques can improve on traditional password authentication, they do not protect against modern threats from Trojans and man-in-the-middle attacks.
Here is an interesting review of new authentication methods, including cognitive passwords, Pass Faces, and various biometric techniques. Although these techniques can improve on traditional password authentication, they do not protect against modern threats from Trojans and man-in-the-middle attacks. Earlier this month, the country of
Earlier this month, the country of  This is an interesting article about fraud schemes that target the elderly. It describes data brokers who collect information about who might be the most vulnerable targets. And it reviews the role of the banks in allowing very weak authentication, unsigned cheques, for financial transactions that drain the victims’ accounts. It is a good example of the link between economics and security — there is lots of money to be made by the data brokers in selling lists to fraud artists, and by the banks in collecting fees for each fraudulent transaction.
This is an interesting article about fraud schemes that target the elderly. It describes data brokers who collect information about who might be the most vulnerable targets. And it reviews the role of the banks in allowing very weak authentication, unsigned cheques, for financial transactions that drain the victims’ accounts. It is a good example of the link between economics and security — there is lots of money to be made by the data brokers in selling lists to fraud artists, and by the banks in collecting fees for each fraudulent transaction. Even careful Internet users are at risk. When a new computer is connected to the Internet, it will be attacked by active scanners within 5 minutes and any vulnerabilities will be exploited. Newer Trojans can also infect users when they simply visit compromised web sites, without the knowledge of the web site owner or the end user. Anti-virus software is not completely effective in detecting these bad programs, and new Trojans are launched every day.
Even careful Internet users are at risk. When a new computer is connected to the Internet, it will be attacked by active scanners within 5 minutes and any vulnerabilities will be exploited. Newer Trojans can also infect users when they simply visit compromised web sites, without the knowledge of the web site owner or the end user. Anti-virus software is not completely effective in detecting these bad programs, and new Trojans are launched every day.